Roblox Mod Apk (Mega Menu, God Mod, Jump, Fly, Unlimited Menu/Robux) v2.607.548

Additional Information Apk
| App Name | Roblox Apk |
| Publisher | Roblox Corporation |
| MOD Info | (Hack Apk, Mega Menu, God Mod, Jump, Fly, Unlimited Menu/Robux ) |
| Size | 171.12 MB |
| Latest Version | V 2.607.548 |
| Price | Free |
| Get it on | |
| Support Device | Android, Tablet |
| Updated | 1 Day Ago |
Elevate your gaming experience to unprecedented heights through the realm of Roblox Mod. As you delve into the realm of Roblox Mod APK, you’re entering a realm where innovation thrives and boundaries fade away. This dynamic platform empowers you to play, create, explore, and connect.
With the power of limitless imagination at your fingertips, Roblox Mod invites you to design captivating worlds, embark on collaborative quests, and redefine social gaming. Prepare to be immersed in a universe where the gaming landscape is yours to shape, and where the only limit is the horizon of your creativity.

Roblox Mod APK
The term Roblox APK Mod pertains to a customized variation of the standard Roblox app, typically found on official app platforms. Roblox is widely recognized for providing a virtual space where users can craft and immerse themselves in various games. The original app is readily downloadable from authorized sources like the Google Play Store, making it accessible to Android devices However, the modded APK, distinct from the version sanctioned by the official developers, is created by external parties.
Are you ready to take your Roblox gaming experience to the next level? Look no further than the Roblox Mod APK, a game modification that opens up a whole new world of possibilities within the popular online platform. With this mod, players can unlock exclusive features, access unlimited resources, and customize their gameplay in ways never before possible.
Whether you’re a seasoned Roblox enthusiast or just dipping your toes into the vast virtual universe, this article is your guide to understanding what the Roblox Mod APK has to offer and how it can revolutionize your gaming journey.
Roblox Beginner Guide: Read more…
Key Features of Roblox Apk
Huge Multiverse of Games: Developing an expansive Roblox multiverse mod entails crafting a collection of interconnected games, providing players with a rich and varied gaming universe to explore and enjoy.
Discover a huge world: Step into the extraordinary realm of the Roblox APK, where a sprawling and one-of-a-kind world beckons, promising unparalleled adventures and discoveries for all who enter.

Gaming Variety: From the excitement of prospecting for gold to engaging in trade, from devising strategies for Warp Drives to setting up Starbases, the opportunities are limitless.
Cooperative Tools: The Roblox login APK Suite is a groundbreaking instrument that facilitates teamwork, promoting the development of an array of games and settings.
Weapon Dynamics: Whether it’s the sheer force of heavy turrets or the tactical positioning of spinals, Roblox offers an abundance of weapon options to suit varying gameplay styles.
Alien Challenges: Confronting alien adversaries brings unexpected hurdles, guaranteeing each gaming session feels unique.
Social Interaction & Emotes: The Social Service function promotes friend invitations while the in-game emote menu allows for individual expression, enriching player communication.
Terrain and Plugin Upgrades: Thanks to the Height map and Color Data Importer, landscapes in Roblox gain enhanced realism. The Cloud-Based Plugin Backups further improve gaming by securing user data.

Multiple chat rooms: Step into the dynamic universe of Roblox APK, offering an array of chat rooms to explore. Engage in lively conversations, connect with fellow enthusiasts, and build connections in uniquely themed interactive spaces.
Enjoy 3D Graphics: Experience the Roblox APK’s captivating world in stunning 3D graphics. Immerse yourself fully as the lifelike visuals enhance your exploration, creativity, and gaming adventure.
Play with your friends: Forge unforgettable memories with your friends using the Roblox APK. Immerse yourselves in an array of captivating virtual experiences, where you can join forces, compete, and create lasting moments together.
Unlimited Robux: Discover limitless potential with the Roblox APK’s unlimited Robux feature. Unleash your creativity, amplify your gaming experience, and realize your dreams without any constraints.
Acquire all upgrades: Unlock the entirety of upgrades with the Roblox APK, granting you complete access to enhancements that will elevate your gaming experience to its zenith, ensuring an unmatched journey in the virtual realm.
More accessible features: Embark on a journey of enhanced accessibility with the Roblox APK, where an innovative spectrum of features awaits. Seamlessly designed for all players, these unique enhancements redefine the way you experience the virtual world.
Fly Hacks for Roblox
The use of fly hacks in Roblox’s Virtual Universe significantly enhances the user experience by granting them a unique sense of liberation. This modification enables the avatars to defy gravity, freely floating and soaring across the game’s diverse imaginative landscapes.
The ability to ascend to new heights and discover unseen corners provides players with an entirely new viewpoint and innovative ways of interacting within the Free Roblox worlds. However, it’s important to remember that while these hacks may be appealing, they could potentially interfere with the genuine gameplay experience with the Roblox hack apk envisioned by the game developers.
How Can I Get Unlimited Robux?
The attraction of Unlimited Robux resonates with the universal yearning to explore without bounds, especially within the expansive and varied world of Roblox. Usually, acquiring Robux, the in-game currency, requires either real-world cash or significant in-game effort.

But with modifications offering Free Robux, players can break free from traditional acquisition constraints and immerse themselves more fully into customization, high-end features, and exploring areas typically hidden behind a paywall. This not only enhances players’ engagement with the game but also adds a dimension of unrestricted exploration and creativity within this vibrant Virtual Universe. However, this modification feature often operates in a legal and ethical twilight zone; thus it is advised that users proceed with caution.
How to Download Roblox Mod Apk Pro version of Fly Hack 2024
Here’s a different way to express the instructions for downloading Roblox Mod Apk from roblxfeed:
To begin with, prepare your Android device for the download by allowing installations from unknown sources. To do this, go to your device’s settings, and scroll down until you find either Security or Privacy options in the menu. A warning message may appear; just affirm your choice.
Next, proceed to download the Roblox MOD APK (Unlimited Robux) from Roblxfeed. Open a web browser on your Android device and navigate to roblxfeed.net. Utilize the search bar on the website to locate the Roblox MOD APK. After finding it, click on it to reach the download page and then press ‘Download’.
Once downloaded, if asked for permission to install apps from unknown sources again, grant it. Finally, after the successful installation of the updated game version with additional content is complete, launch and enjoy!
System Requirements of Roblox MOD APK
For online play, ensure your Android device runs at least version 5.0 and has a minimum of 2GB RAM. Also, you’ll need to have a minimum of 140MB of free space and an internet connection.
Roblox Beginner Guide: Read more…
Most Popular Roblox Games to Play With Friends
- Adopt Me!
- MeepCity
- Jailbreak
- Brookhaven
- Tower of Hell
- Brookhaven Rp
- Blox Fruits
- Piggy
- Arsenal
- Royale High
- Mad City
- Natural Disaster Surviva

Adopt Me!:
Step into the virtual world of pet adoption and care. Adopt Me! allows players to raise and trade virtual pets, decorate homes, and engage in various activities, creating a heartwarming and interactive experience. Read more...
MeepCity:
In MeepCity, players can socialize, play minigames, and customize their avatars while interacting with others in a vibrant virtual city. The game’s mix of activities offers a dynamic and engaging environment. Readmore..
Jailbreak:
Jailbreak thrusts players into the roles of criminals or law enforcement officers. Criminals plot heists while police officers strive to maintain order. Read more…
Brookhaven:
Experience life in a suburban town as you explore different locations, interact with fellow players, and partake in various role-playing scenarios. Brookhaven offers an immersive environment for those seeking virtual community experiences. Read more…
Tower of Hell:
Test your skills and perseverance in Tower of Hell, a challenging platformer where players navigate a series of increasingly difficult obstacles. The game’s competitive nature keeps players engaged in conquering new heights.
Piggy:
Piggy combines horror and strategy in a story-driven adventure where players solve puzzles to uncover the mysteries behind the infected characters. With an unfolding narrative, Piggy offers both excitement and intrigue.
Arsenal:
Engage in fast-paced shooter action in Arsenal, where players eliminate opponents to earn new weapons.
Royale High:
Royale High provides players with a magical school experience, complete with customizable characters, fashion, and roleplaying. Attend classes, explore the campus, and partake in enchanting quests. Read more…
Mad City:
Live the life of a criminal or a superhero in Mad City, a game that offers an open-world environment where players can choose their path. Engage in heists, missions, and car chases as you carve your own story.
Natural Disaster Survival:
Survive various natural disasters in this game, where players must navigate through earthquakes, floods, and other challenges to stay alive. Quick thinking and strategic choices are essential for success.
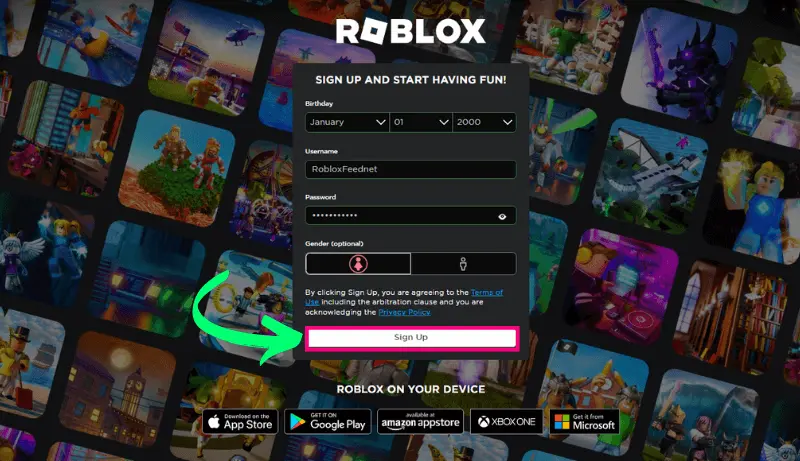
How to Download And Install Roblox Mod APK
You must follow these steps to download and install the Roblox Mod APK:
Secure the Mod APK: You will visit the download button collect the the Roblox Mod APK file from https://roblxfeed.net/ and then forward step by step.
Install the Mod APK: Open the downloaded APK file and follow the following steps.
Permissions Check: Grant any necessary permissions during installation.
Launch the Mod: Discover the application icon and initiate the Roblox Mod Menu APK.
Experience the Mods: Log in using your Roblox Account and enjoy the distinct features provided by the mod. Free Roblox Accounts Readmore…

Why is Roblox So Popular?
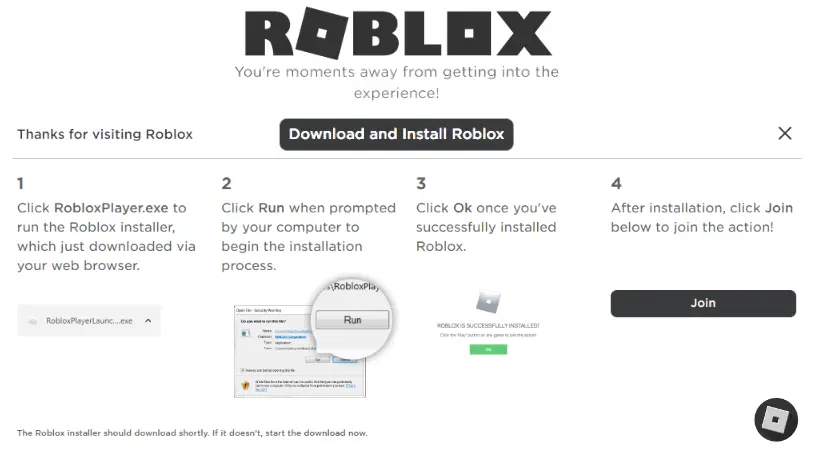
How to Install Roblox On PC
Certainly, here’s a polished version of the steps to install Roblox on your PC:
- Visit Website: Open your web browser and navigate to the official Roblox website: Roblox
- Download Roblox Player: You will receive a notification to acquire the Roblox Player. You must click on the “Download & Install” button to move next step.
- Run the Installer: You will press double-click on it to start the installation.
- Follow Installation Instructions: Follow the installation prompts, choose an installation location if prompted, and agree to the terms and conditions.
- Launch Roblox: Following the installation, the Roblox Player might open automatically. If not, you can locate the Roblox Player icon on your desktop or in the Start menu.
- Log In and Start Playing: Open the Roblox Player, log in with your account details, and immerse yourself in the diverse range of games available.
You’re now all set to enjoy the captivating world of Roblox on your PC!
Faq’s (Frequently Asked Question)
What is Roblox?
Roblox is a popular online platform for creating, playing, and sharing user-made games. Players can customize avatars and explore a wide range of games, all created by the community. And Readmore..
Is there a Roblox mod?
Roblox lacks standard mods but provides in-platform tools for creativity. External mods breach terms of service and harm accounts; here you will download the Roblox mod APK every time.
What is God mode in Roblox mobile?
In Roblox mobile, “God mode” is a cheat for invincibility, but using it breaks rules and can result in account problems.
Can I access free Robux with Roblox Mod APK here?
Of course, you can use a Roblox Mod APK to get free Robux against the rules which can harm your account.
Can Roblox Mod Apk be available with multiplayer games?
Roblox Mod Apks are not legitimate for multiplayer games and can lead to account risks.
Conclusion
A Roblox Mod APK is a modded version of the Roblox mobile app, offering unauthorized features such as cheats or shortcuts for in-game currency like Robux. It’s important to know that using such mods goes against Roblox’s rules. To ensure the best and safest experience, it’s strongly advised to stick with the official Roblox app and play within the established guidelines. Your account’s security and enjoyment are best preserved by playing by the rules.
The Roblox Mod APK Unlimited Robux provides an enhanced and seamless gaming experience for Roblox enthusiasts. It allows players to unlock exclusive features, helps them advance in their games, and offers endless possibilities with unlimited Robux. Always ensure you download from a trusted source to safeguard your device against malicious software. Start exploring new dimensions in your gameplay today by trying out the Roblox Mod APK